Ingress¶
What is Ingress?¶
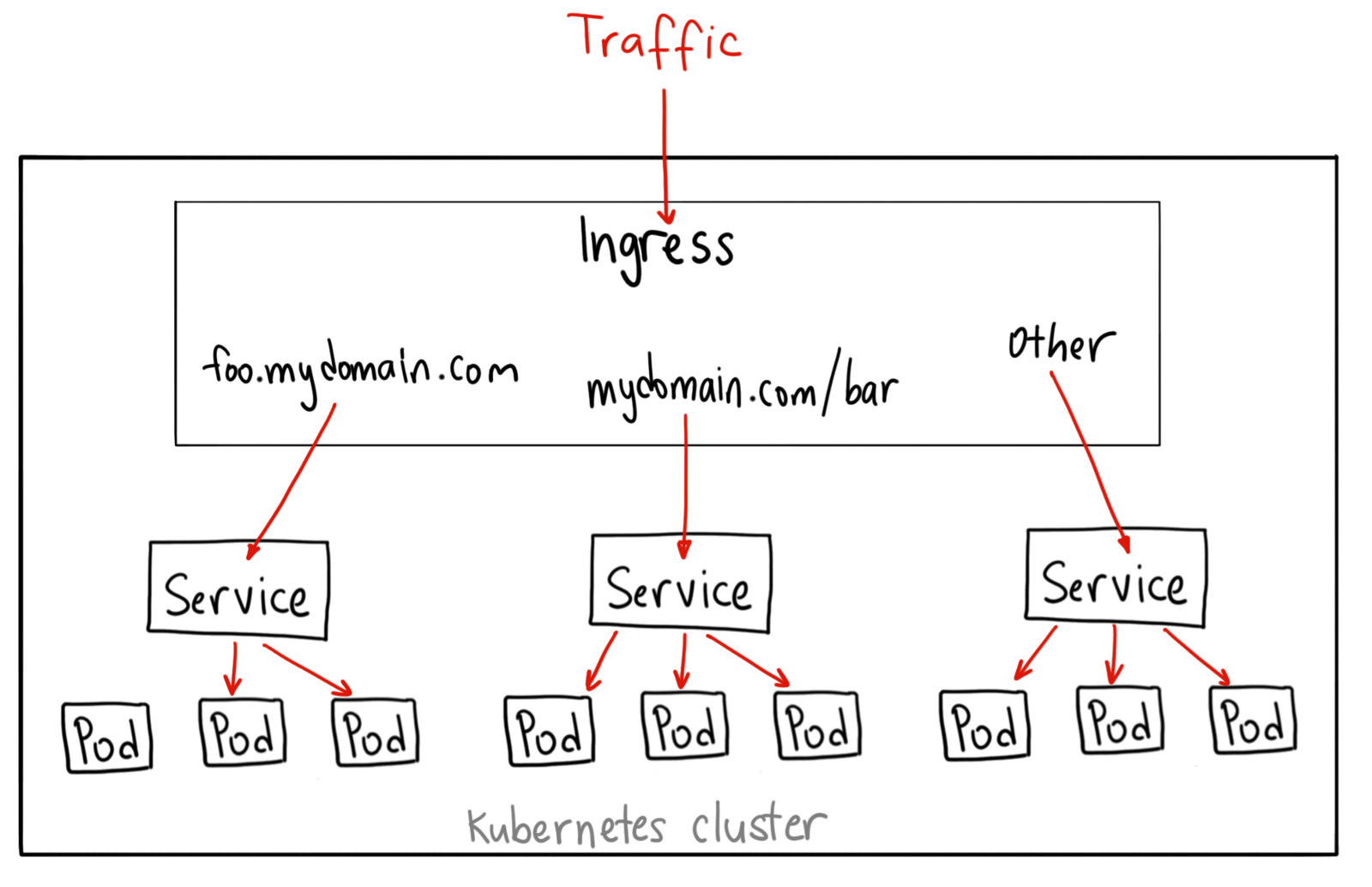
Traditionally, you would create a LoadBalancer service for each public system you want to expose. This can get rather expensive. Ingress gives you a way to route requests to services based on the request host or path, centralizing a number of services into a single entrypoint.
You can do a lot of different things with an Ingress, and there are many types of Ingress controllers that have different capabilities.
An ingress can be configured to give services externally-reachable URLs, load balance traffic, terminate SSL, and offer name based virtual hosting. An ingress controller is responsible for fulfilling the ingress, usually with a loadbalancer, though it may also configure your edge router or additional frontends to help handle the traffic.
An ingress does not expose arbitrary ports or protocols. Exposing services other than HTTP and HTTPS to the internet typically uses a service of type Service.Type=NodePort or Service.Type=LoadBalancer.
Ingress Controller¶
In order for the ingress resource to work, the cluster must have an ingress controller running. Ingress Controllers can technically be any system capable of reverse proxying, but the most common is Nginx. There are many types of Ingress controllers, from the Google Cloud Load Balancer, Nginx, Contour, Istio, and more. There are also plugins for Ingress controllers, like the cert-manager, that can automatically provision SSL certificates for your services.
Nginx Ingress Controller¶
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/mandatory.yaml
Then for AWS L4 ELB:¶
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/provider/aws/service-l4.yaml
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/provider/aws/patch-configmap-l4.yaml
To configure the load balancer as internal ELB add the following annotation to the service-l4.yaml
service.beta.kubernetes.io/aws-load-balancer-internal: "0.0.0.0/0"
To add TLS certificate the ELB, add the following annotation to the service-l4.yaml
service.beta.kubernetes.io/aws-load-balancer-ssl-cert: arn:aws:acm:eu-central
service.beta.kubernetes.io/aws-load-balancer-ssl-ports: "443"
service.beta.kubernetes.io/aws-load-balancer-backend-protocol: tcp
Sample Ingress controller Sevice.yaml file. In this example, the ELB off loads the SSL, and Both http and https forwarded to http port of containers.
kind: Service
apiVersion: v1
metadata:
name: ingress-nginx
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
# Enable PROXY protocol
service.beta.kubernetes.io/aws-load-balancer-proxy-protocol: "*"
# Ensure the ELB idle timeout is less than nginx keep-alive timeout. By default,
# NGINX keep-alive is set to 75s. If using WebSockets, the value will need to be
# increased to '3600' to avoid any potential issues.
service.beta.kubernetes.io/aws-load-balancer-ssl-cert: "arn:aws:acm:us-west-2:507987312224:certificate/620d620f-c058-4f35-ba74-cdbb4b1681c0"
service.beta.kubernetes.io/aws-load-balancer-connection-idle-timeout: "60"
service.beta.kubernetes.io/aws-load-balancer-internal: 0.0.0.0/0
service.beta.kubernetes.io/aws-load-balancer-ssl-ports: "443"
service.beta.kubernetes.io/aws-load-balancer-backend-protocol: "tcp"
spec:
type: LoadBalancer
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
ports:
- name: http
port: 80
targetPort: http
- name: https
port: 443
targetPort: http
For AWS L7 ALB:¶
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/provider/aws/service-l7.yaml
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/provider/aws/patch-configmap-l7.yaml
Writing access logs to an S3 bucket is a standard feature of ELBs. For LoadBalancer Services this can also be configured using Annotations.
metadata:
annotations:
service.beta.kubernetes.io/aws-load-balancer-access-log-enabled: true
# The interval for publishing the access logs (can be 5 or 60 minutes).
service.beta.kubernetes.io/aws-load-balancer-access-log-emit-interval: 60
service.beta.kubernetes.io/aws-load-balancer-access-log-s3-bucket-name: my-logs-bucket
service.beta.kubernetes.io/aws-load-balancer-access-log-s3-bucket-prefix: logs/prod